Introduction
Enterprise challenges we solve
Reliance Cyber’s Managed SASE directly addresses key enterprise pain points across the UK:
Disconnected tools and excessive management overhead
Poor user experience in hybrid or remote environments
Expensive, inflexible MPLS networks
Security blind spots from shadow IT or cloud sprawl
Inconsistent policy enforcement and compliance risk
Difficult-to-scale legacy infrastructure
THE EXPLANATION
What is SASE?
Understanding the evolution and components of Secure Access Service Edge
- Overview
- Evolution
- Components
- vs Traditional
- SASE vs SSE
Gartner Definition
The Future of Network Security
Secure Access Service Edge (SASE) represents a fundamental shift in how organizations approach network security and connectivity. Coined by Gartner in 2019, SASE converges wide-area networking (WAN) and network security services into a single, cloud-delivered service model.
SASE addresses the reality of today’s hybrid workforce, cloud-first applications, and distributed infrastructure by delivering networking and security as a unified cloud service.
Cloud-Native Architecture
Built for the cloud era, not retrofitted from legacy systems
Converged Services
Networking and security unified in a single platform
Identity-Centric
Security follows the user, not the network perimeter
SASE at a Glance
Key benefits and capabilities of our Managed SASE solution
85+
Global Points of Presence
Up to 50%
Network Cost Reduction
10Gbps
Per Tunnel Performance
6x
Integrated Security Services
The evolution to SASE
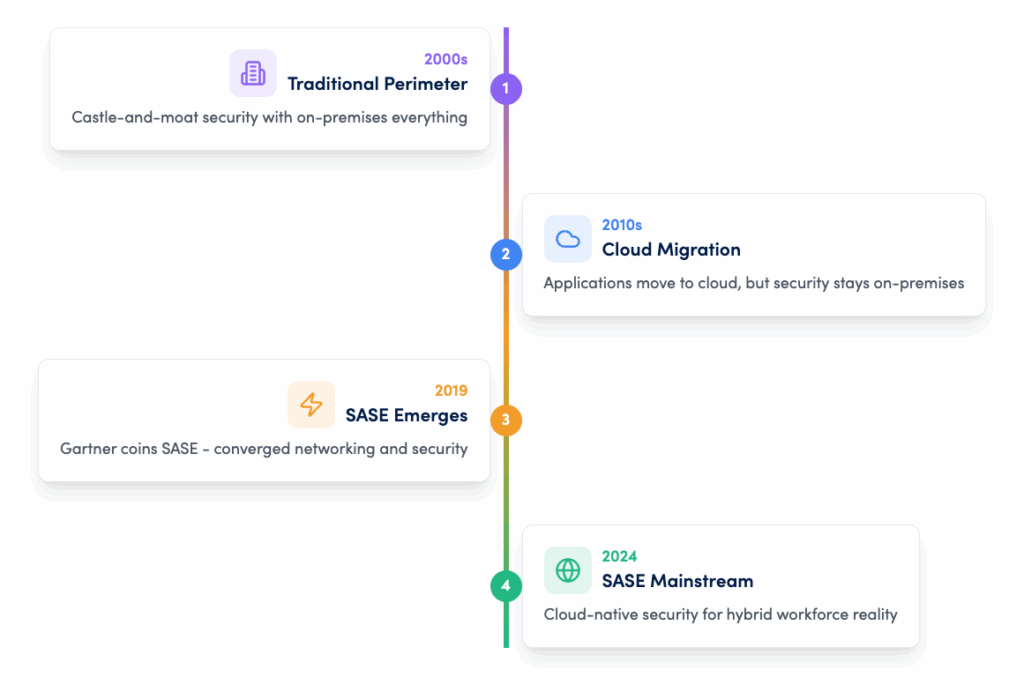
SD-WAN
Software-defined networking for optimised connectivity
DNS
Secure DNS resolution with threat intelligence and filtering
Cloud On-Ramp Connectivity
Direct, optimised access to cloud services (AWS, Azure, GCP)
SWG
Secure web gateway for internet protection
FWaaS
Next-generation firewall as a service
Global Private Backbone
High-performance global network infrastructure
Traditional VPN architecture VS SASE unified architecture
| ASPECT | TRADITIONAL | SASE |
|---|---|---|
| Architecture | Hardware appliances in data centers | Cloud-native, globally distributed |
| Scalability | Manual provisioning, limited capacity | Elastic, auto-scaling on demand |
| Management | Multiple consoles, complex policies | Single pane of glass, unified policies |
| Performance | Backhauling through data center | Direct cloud access, optimized paths |
| Cost | High CAPEX, ongoing maintenance | OPEX model, reduced overhead |
Traditional Challenges
- Complex multi-vendor management
- Poor remote user experience
- High infrastructure costs
- Slow deployment cycles
SASE Advantages
- Single pane of glass management
- Optimized cloud performance
- Reduced operational overhead
- Rapid, elastic scaling
In comparison…
| FEATURE | SASE (Secure Access Service Edge) | SSE (Security Service Edge) |
|---|---|---|
| Definition | Full convergence of networking and security | Cloud-delivered security only |
| SD-WAN | Yes – integrated | No |
| Global Backbone | SLA-backed private backbone | Depends on public internet/MPLS |
| Security Stack | Full: ZTNA, FWaaS, SWG, CASB, DLP, IPS | Same as SASE |
| Ideal Use Case | Modernise both network and security | Enhance cloud security on existing network |
| Cost | Higher but replaces multiple tools and services | Lower upfront but may require other investments |
WHY RELIANCE CYBER?
Security that moves your business forward
At Reliance Cyber, we don’t just deploy technology — we deliver outcomes. From day one, our managed SASE and security services are designed to reduce risk, accelerate transformation, and free your teams to focus on what matters most.
What you get
Faster time to value
Go live in days, not months — thanks to engineering-led delivery and automation-first deployment.
Outcome: Quickly realise value from your investment, reduce project delays, and support fast-changing business needs.
Click for technical implementation:
- Infrastructure-as-Code for automated provisioning
- Pre-built templates and configuration libraries
- DevSecOps pipelines for rapid, consistent deployments
- Automated testing and validation workflows
- Cloud-native architecture eliminating hardware dependencies
Reduced risk from day one
Security controls built on decades of MDR and IR experience are embedded from the start.
Outcome: Immediate protection against known and unknown threats with Cato Networks’ proven SASE platform — no “warm-up” period required.
Click for technical implementation:
- Real-world attack patterns built into preventative controls by default
- MDR threat intelligence feeds integrated into SASE policies for proactive blocking
- MDR-derived detection rules
- Incident response playbooks automated in SOAR platform
- Continuous policy updates based on latest threat landscape
Smarter, quicker threat response
Autonomous detection and response cuts incident dwell time from hours to seconds.
Outcome: Avoid costly breaches, contain threats faster, and reduce impact on operations.
Click for technical implementation:
- AI-powered behavioural analytics and anomaly detection
- Automated containment and isolation capabilities
- SOAR integration for orchestrated response workflows
- Real-time correlation across SASE, EDR, SIEM & Vulnerability Management data
Less operational overhead
Proactive monitoring, integrated platforms, and streamlined support reduce internal workload.
Outcome: Fewer tickets, less firefighting, and more time for strategic IT initiatives.
Click for technical implementation:
- Single pane of glass management console
- Automated policy deployment and configuration management
- Proactive health monitoring
- Self-healing network with automatic failover
Ongoing service excellence
Regular reporting, reviews, and strategic guidance to ensure continuous improvement and value realisation.
Outcome: Continuous optimisation, proactive issue resolution, and strategic alignment with business objectives.
Click for service management framework:
- Monthly Service Reporting: Detailed performance metrics, security posture, and utilisation analytics
- Fortnightly Service Reviews: Technical health checks, policy optimisation, and proactive recommendations
- Quarterly Business Reviews: Strategic alignment sessions with senior stakeholders and roadmap planning
- Designated Customer Success Manager: Single point of contact for escalations and strategic guidance
- 24/7 UK-based Support: Direct access to L3 engineers with no tier 1/2 delays
Strategic business enablement
Purpose-built solutions for your specific business goals and compliance requirements.
Outcome: Accelerate digital transformation whilst maintaining security and compliance.
Click to see how we enable your goals:
- Cloud Transformation: Rapid, secure deployment
- Cyber Resilience: Integrated detection & response
- Cost Reduction: MPLS replacement, vendor consolidation
- Legacy Modernisation: DevSecOps-led infrastructure-as-code
- Governance: Custom policies, direct engineer access
Trusted technology partners
Delivering enterprise-grade solutions with industry-leading platforms




Let’s Talk Results
Reliance Cyber isn’t just a provider, we’re your outcome-driven partner in securing and accelerating your digital strategy. Talk to us about reducing your risk, cost, and complexity — without slowing down your business.
Enhanced security add-on services
Extend your SASE deployment with additional security services for comprehensive protection
- Managed Detection & Response (MDR)
Comprehensive threat lifecycle management. Complete threat protection with 24/7 expert oversight. - Zero Trust Network Access (ZTNA)
Secure application access without VPNs. Replace legacy VPNs with modern, secure access controls. - Cloud Access Security Broker (CASB)
Comprehensive cloud application security. Secure cloud applications and prevent data loss. - Digital Experience Monitoring (DEM)
Gain visibility into user experience and performance. Ensure optimal performance for remote workers.
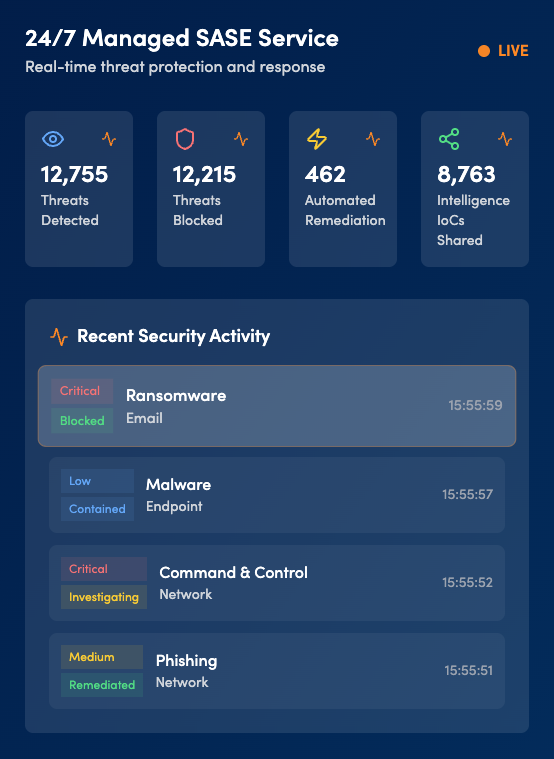
Managed Detection & Response (MDR)
Comprehensive threat lifecycle management
Service Overview
Our comprehensive MDR service combines advanced threat detection, security orchestration, extended detection and response, and threat intelligence into a unified platform. With 24/7 monitoring from our UK-based SOC, automated response capabilities, and expert threat hunting, we provide complete protection across your entire digital estate.
Key Features
- 24/7 UK-based Security Operations Centre monitoring
- Advanced threat hunting and behavioral analytics
- Automated security orchestration and response (SOAR)
- Cross-platform threat correlation (XDR)
- Real-time threat intelligence integration
- Incident investigation and forensic analysis
- Automated playbook execution and response
- Compliance reporting and documentation
Managed Detection & Response (MDR) in Action
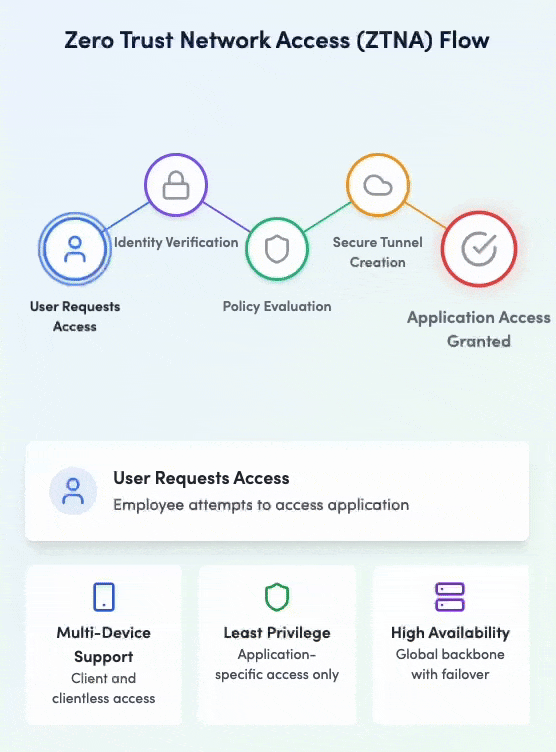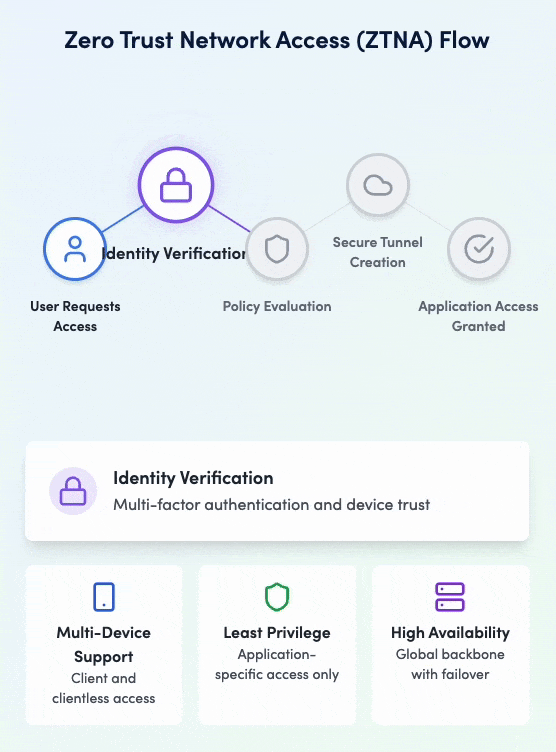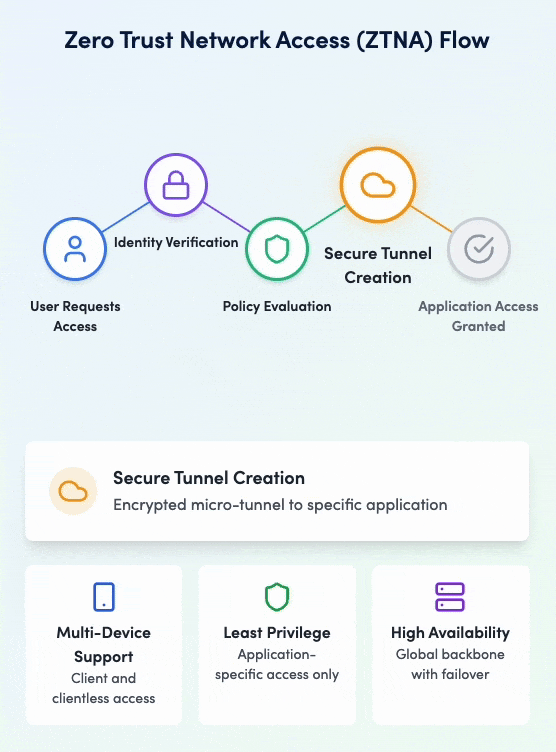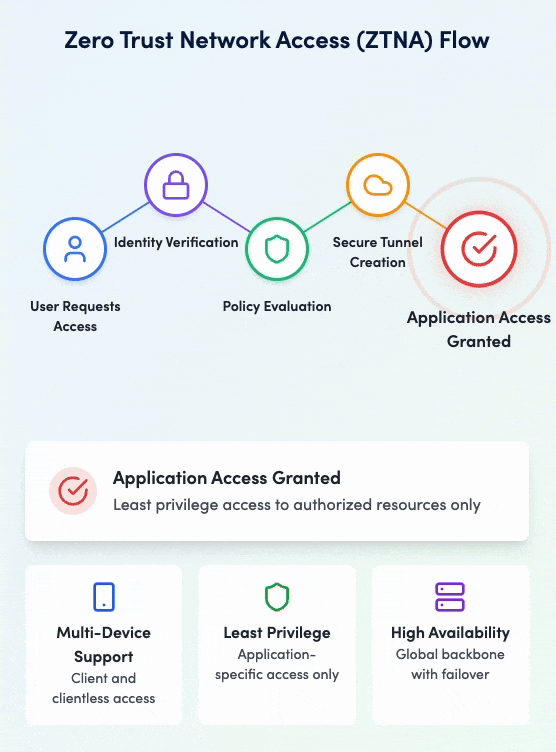
Zero Trust Network Access (ZTNA)
Secure application access without VPNs
Service Overview
Implement true Zero Trust access with granular application-level controls. Our ZTNA solution provides secure, direct access to applications without exposing your network, ensuring users only access what they need based on identity, device, and context.
Key Features
- Application-specific access controls
- Device trust and compliance verification
- Identity-based access policies
- Micro-segmentation and least privilege
- Seamless user experience across devices
- Real-time access policy enforcement
- Comprehensive access logging and analytics
- Integration with identity providers
Zero Trust Network Access in action
Cloud Access Security Broker (CASB)
Comprehensive cloud application security
Service Overview
Gain visibility and control over cloud application usage with our comprehensive CASB solution. Monitor, secure, and govern access to cloud services while preventing data loss and ensuring compliance across your cloud ecosystem.
Key Features
- Cloud application discovery and visibility
- Data loss prevention (DLP) policies
- Real-time threat protection for cloud apps
- Compliance monitoring and reporting
- Shadow IT discovery and governance
- API-based and proxy-based protection
- User behavior analytics for cloud access
- Automated policy enforcement
Cloud Access Security Broker in action
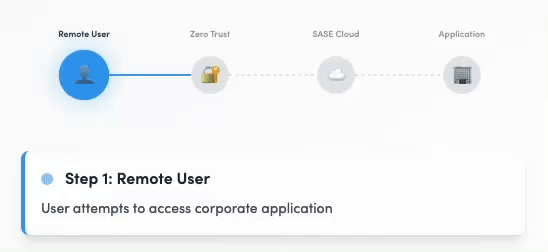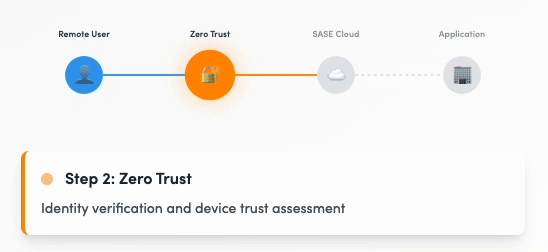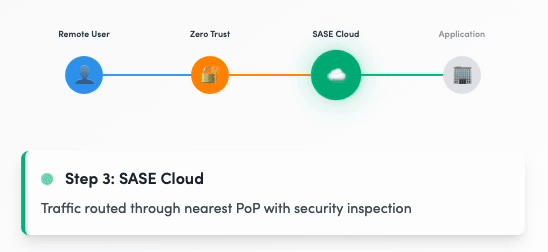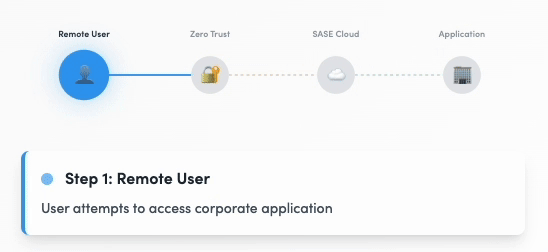
Digital Experience Monitoring (DEM)
Gain visibility into user experience and performance
Service Overview
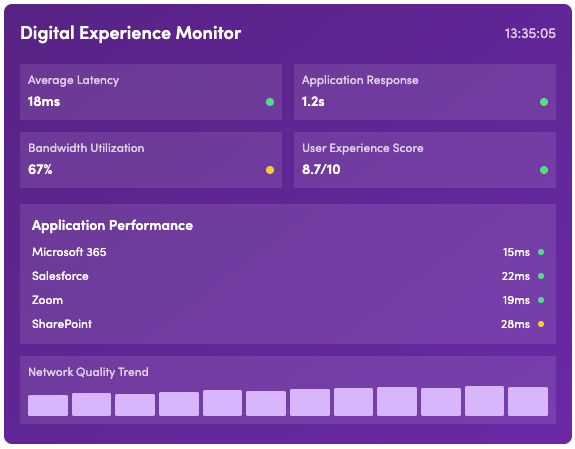
Monitor the digital experience of your users with deep insights into application performance, network conditions, and user satisfaction. Quickly identify and troubleshoot issues before they affect productivity.
Key Features
- Real-time application performance monitoring
- Network path visibility and diagnostics
- User experience scoring and analytics
- Proactive issue detection and alerting
- Bandwidth usage insights
- Application response time tracking
- End-to-end transaction monitoring
- Performance benchmarking and reporting
Digital Experience in Action
IN DETAIL
Frequently asked questions
How quickly can SASE be deployed?
Our managed SASE service powered by Cato Networks can typically be deployed within 2 days using our Infrastructure-as-Code approach. This includes SASE technology deployment, policy deployment and service integration.
What’s included in 24/7 monitoring?
Our UK-based, SC-cleared SOC provides continuous monitoring of your SASE environment, including threat detection and incident response while our NOC Continuously manages policy enforcement and performance monitoring.
How does SASE reduce costs compared to traditional networking?
SASE eliminates the need for multiple point solutions, reduces MPLS costs by up to 50%, minimises hardware requirements, and significantly reduces operational overhead through centralised management.
What happens to our existing security technologies?
We provide a comprehensive roadmap strategy that can help with migration of existing security technologies, by consolidating your security technologies your redundant solutions are no longer required and therefore reduce complexity and cost.



